Entra / Azure SSO Setup Guide
Providing documentation to your users on how to set up SSO with Entra is important for a smooth integration process. To make the process easier for your customers we provide a configuration specific to Entra, allowing you to skip collecting the OIDC URLs and instead just collect a Tenant ID.
const result = await client.sso.management.createOidcClient({ redirectUrl: "https://app.example.com/authorization-code/callback", customerId: "your_customer_id", idpInfoFromCustomer: { idpType: "MicrosoftEntra", tenantId: "b17958...", clientId: "5c891426-22...", clientSecret: "aNb8Q~-v2R...", usesPkce: true, },});from propelauth_byo.generated.idp_info_from_customer import IdpInfoFromCustomerMicrosoftEntra
result = await client.sso.management.create_oidc_client( redirect_url="https://app.example.com/authorization-code/callback", customer_id="your_customer_id", idp_info_from_customer=IdpInfoFromCustomerMicrosoftEntra( tenant_id="b17958...", client_id="5c891426-22...", client_secret="aNb8Q~-v2R...", uses_pkce=True, ),)CreateOidcClientResponse result = client.sso.management.createOidcClient( CreateOidcClientCommand.builder() .redirectUrl("https://app.example.com/authorization-code/callback") .customerId("your_customer_id") .idpInfoFromCustomer( IdpInfoFromCustomer.MicrosoftEntra.builder() .tenantId("b17958...") .clientId("5c891426-22...") .clientSecret("aNb8Q~-v2R...") .usesPkce(true) .build() ) .build());var result = await client.Sso.Management.CreateOidcClientAsync(new CreateOidcClientCommand{ RedirectUrl = "https://app.example.com/authorization-code/callback", CustomerId = "your_customer_id", IdpInfoFromCustomer = new IdpInfoFromCustomerMicrosoftEntra { TenantId = "b17958...", ClientId = "5c891426-22...", ClientSecret = "aNb8Q~-v2R...", UsesPkce = true }});Below is an example guide of what this documentation could look like, as well as how to collect the Tenant ID from your users.
-
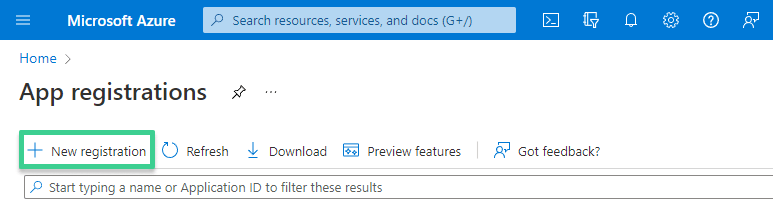
Begin by logging into your Entra admin console and navigating to the “App Registrations” section.
-
Name the application and select Accounts in this organizational directory only as the supported account type.
-
In the Redirect URI section, select Web and enter the redirect URI for your app (e.g.,
https://myapp.com/callback). See here for more details on the callback URL that you should provide to your users.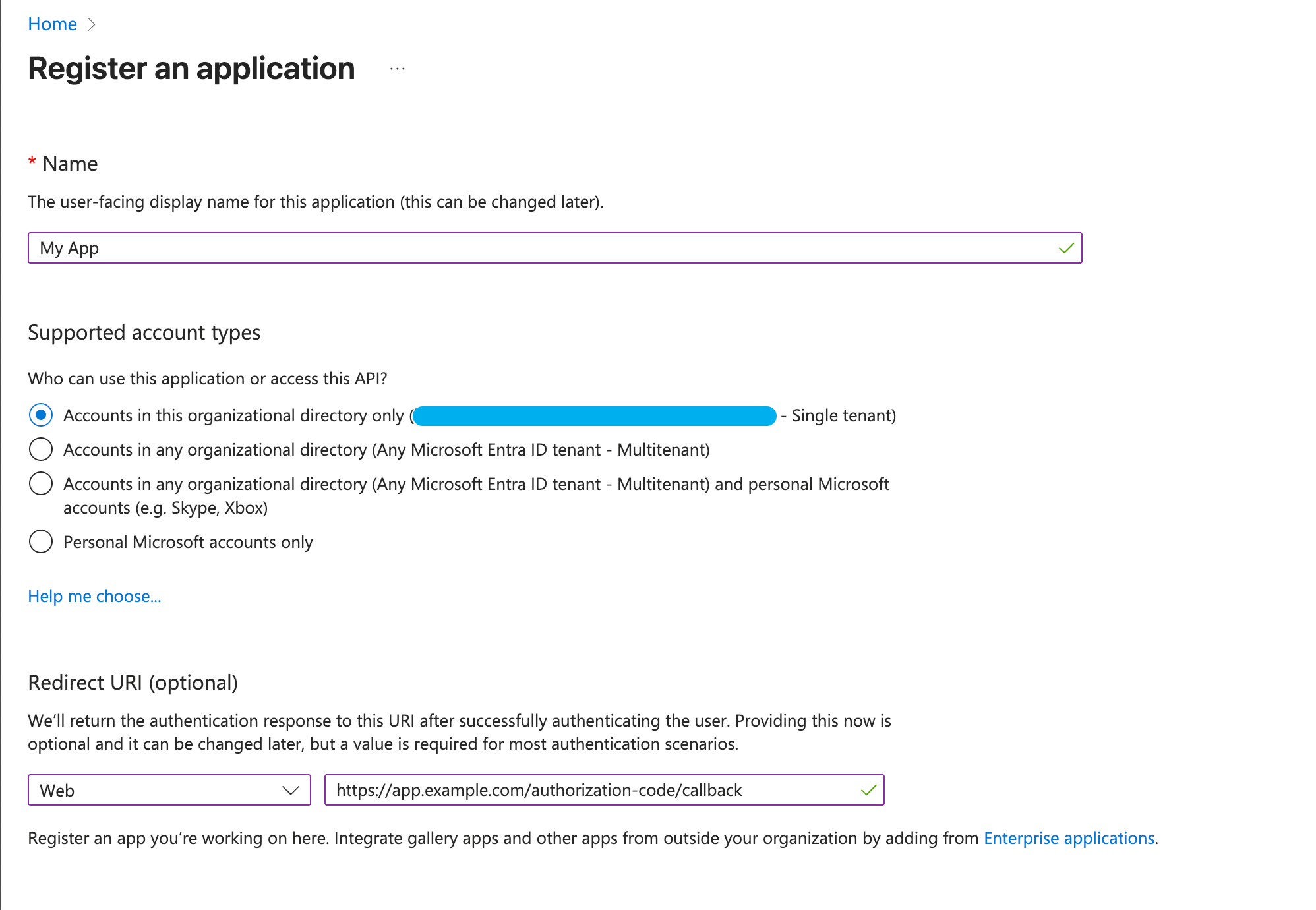
-
On the next page, copy and paste the Application (client) ID and Directory (tenant) ID into
{your application}.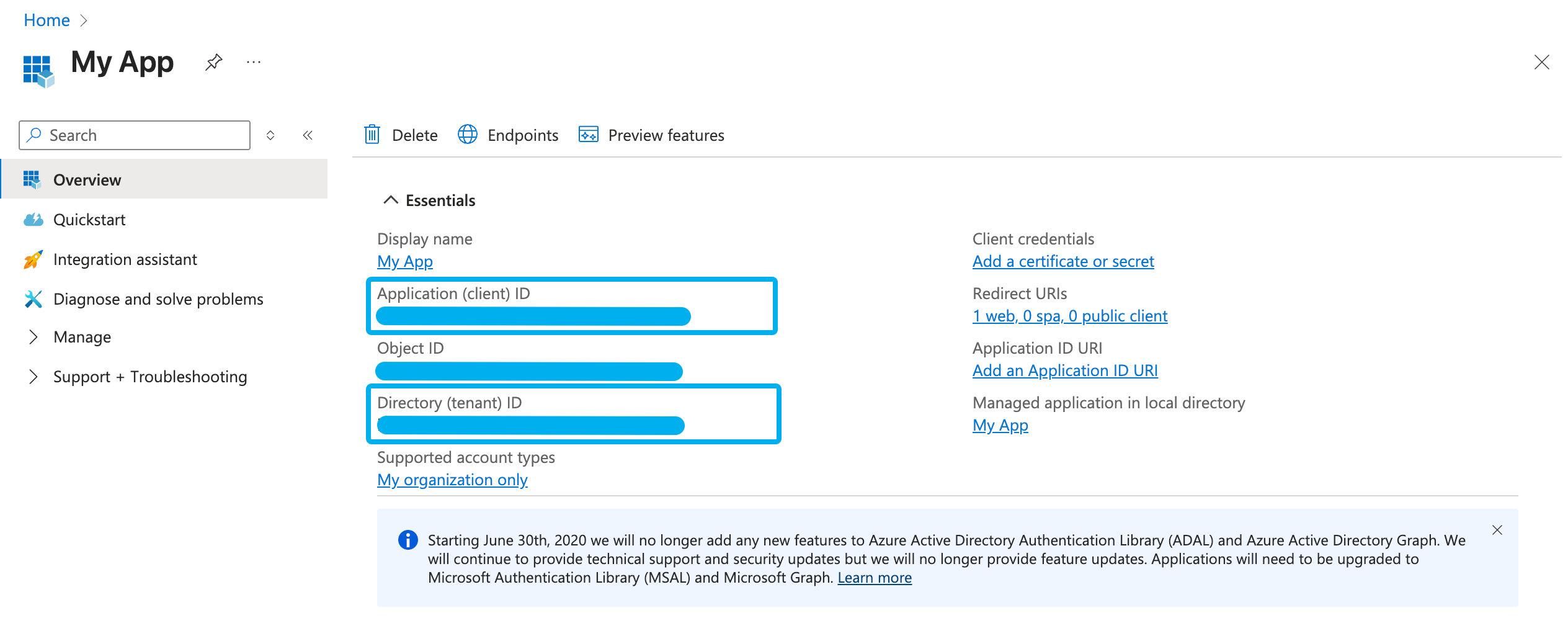
-
Next, click on Manage in the sidebar followed by Certificates & secrets.
-
Click New client secret.
-
Add a description and set an expiration period for the Client Secret, then click Add. Note that you will need to generate a new Client Secret when this one expires.
-
Copy the Value of the Client Secret and paste it into
{your application}as the Client Secret.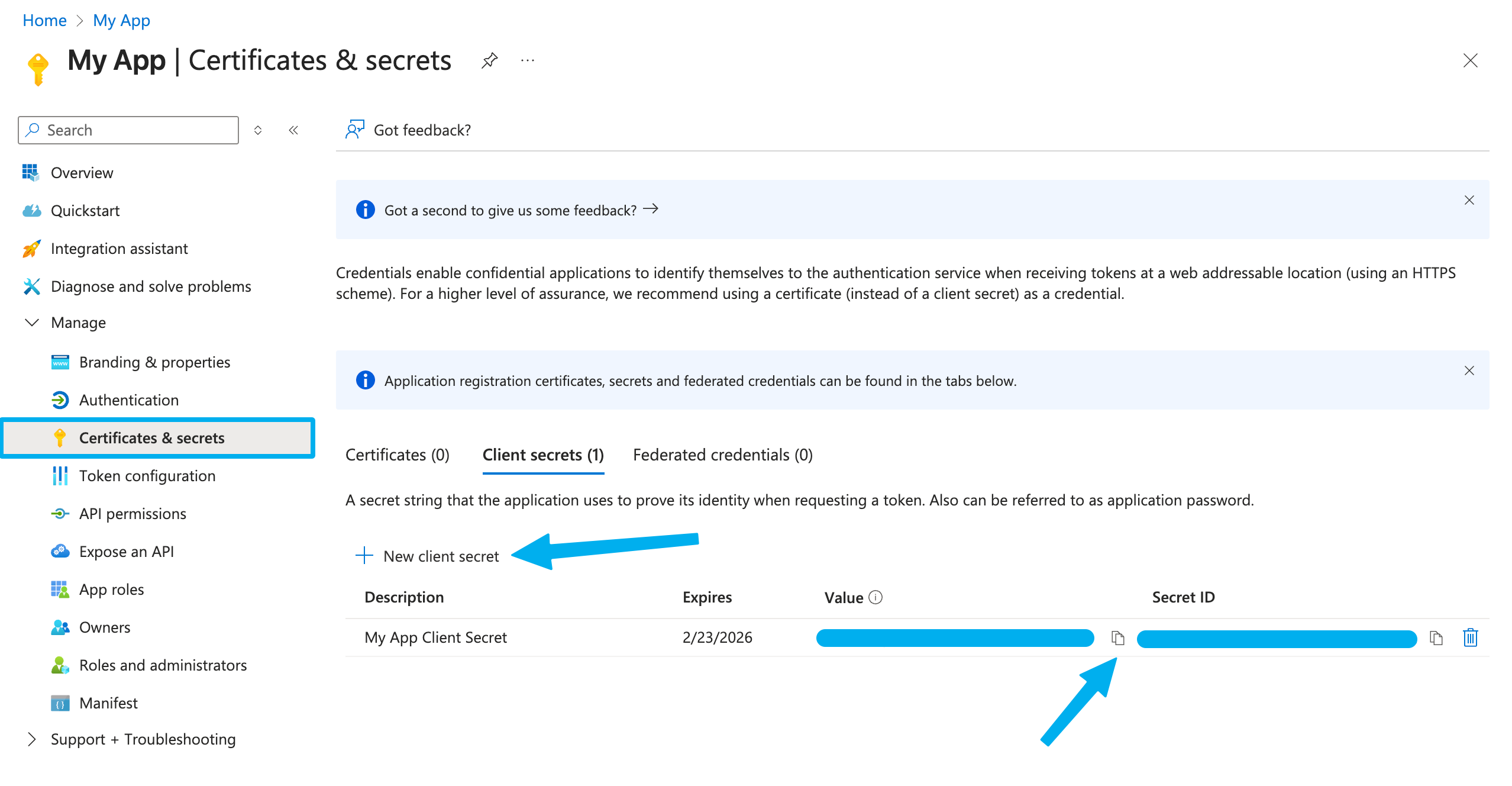
-
Click Save in
{your application}.