Managing SCIM Connections
Managing and troubleshooting your customer’s SCIM connections is an important part of providing a smooth integration experience for your users. This guide will go through some best practices when using SCIM as well as some troubleshooting tips for common problems you may run into.
SCIM Dashboard
Section titled “SCIM Dashboard”The SCIM Dashboard provides a centralized view of all your customer’s active SCIM connections, allowing you to manage users and groups within each connection.
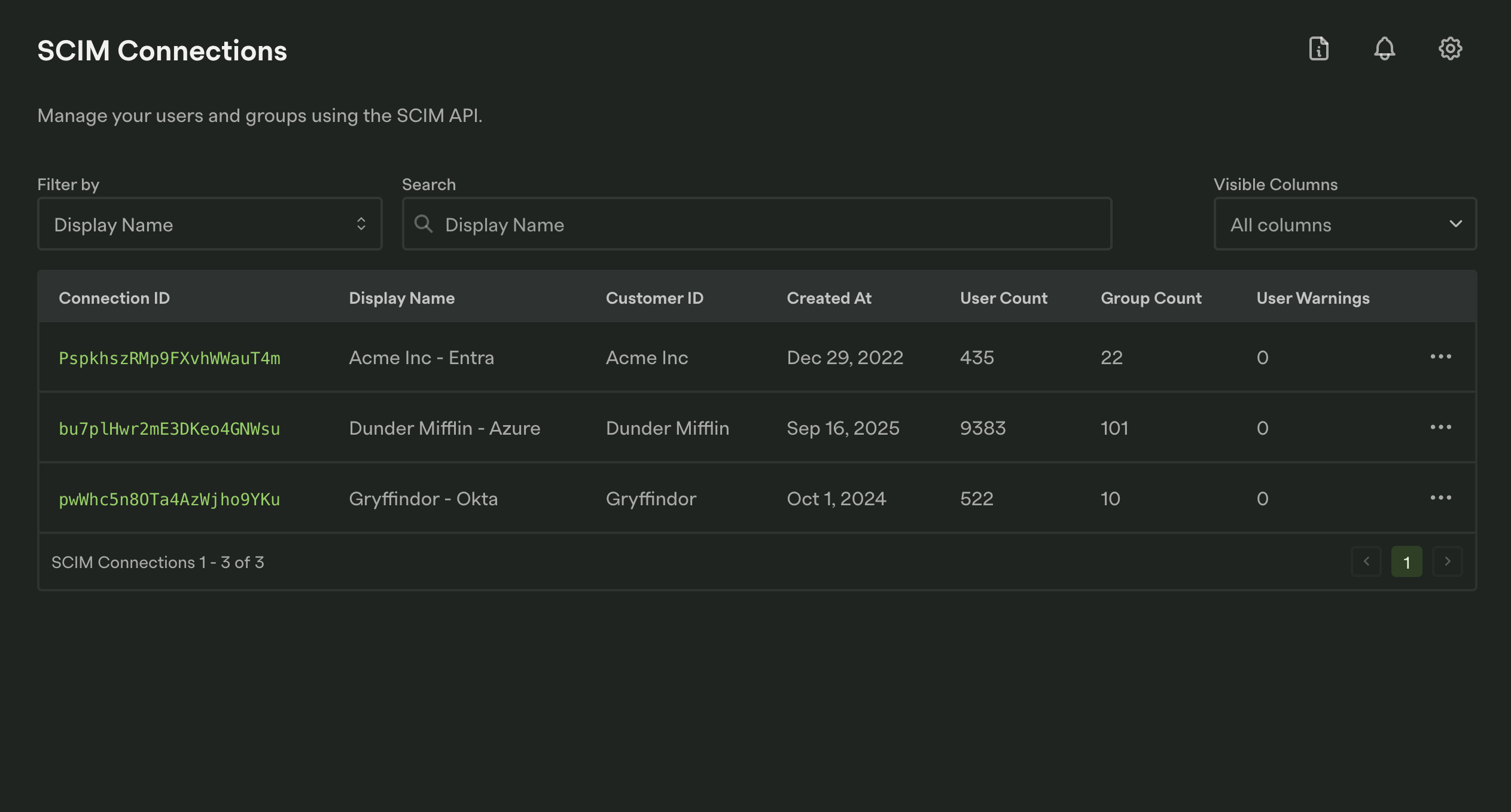
Within each connection are users and groups that were synced from your customer’s identity provider. Additionally, each connection has a Mapping configuration that can be mapped in the Dashboard.
Updating Mapping Configurations in the Dashboard
Section titled “Updating Mapping Configurations in the Dashboard”Sometimes properties are not where we expect them to be. You might expect a field favoriteColor to be at the top level of the SCIM user object, but this customer accidentally sent it as favorite_color or preferences.favoriteColor.
Fortunately, the Dashboard can help you debug and fix these issues, without needing to write custom code or go back to your customer to ask them to fix it.
The mapping has a setting called Warn if missing for each property. When enabled, if your customer sends a user or group that is missing that property, a warning will be created in the Dashboard. You can see both how many warnings exist for a given connection on the SCIM Connections page, as well as find example requests where the property was missing.
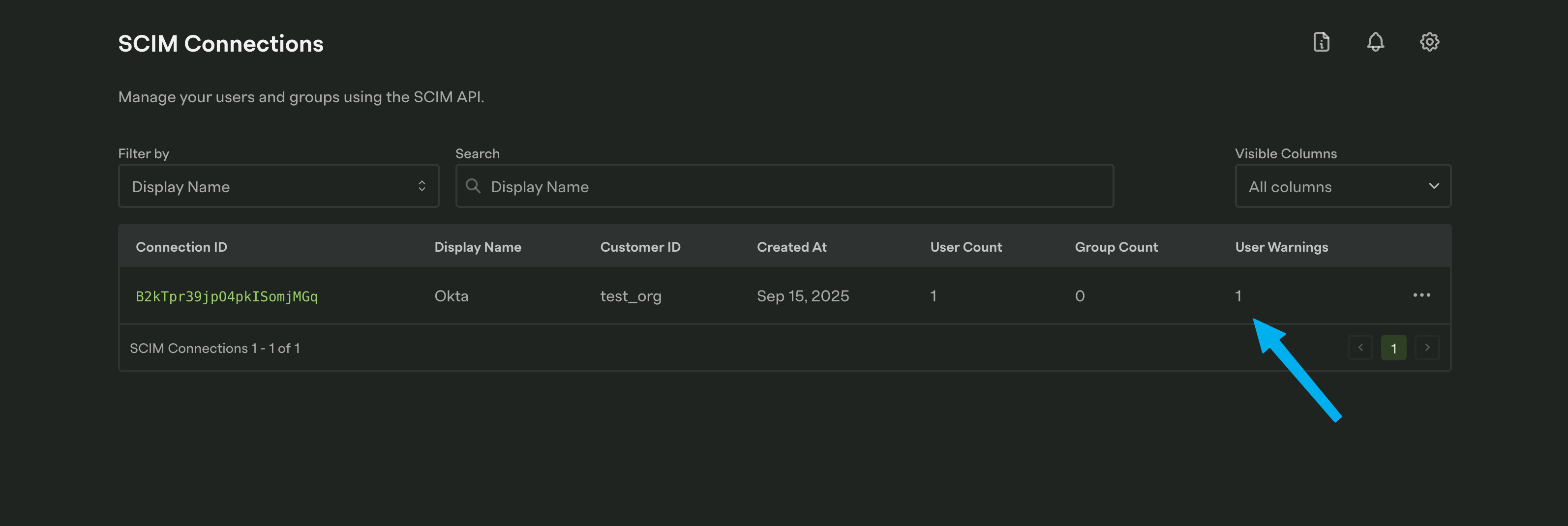
Click on the connection and then Users with Warnings for a list of users in that SCIM connection who have open warnings. For even more information, click on one of the users.
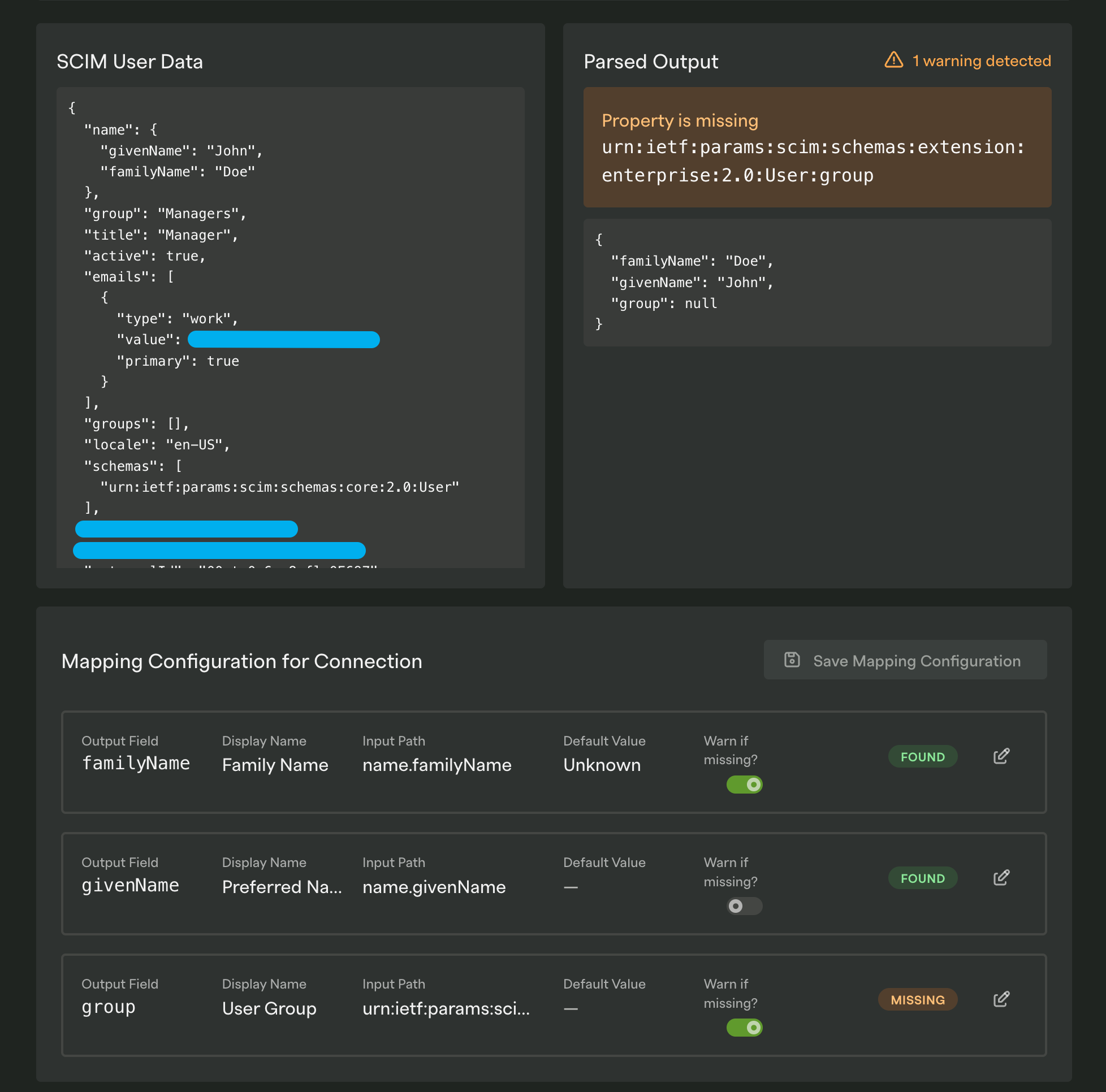
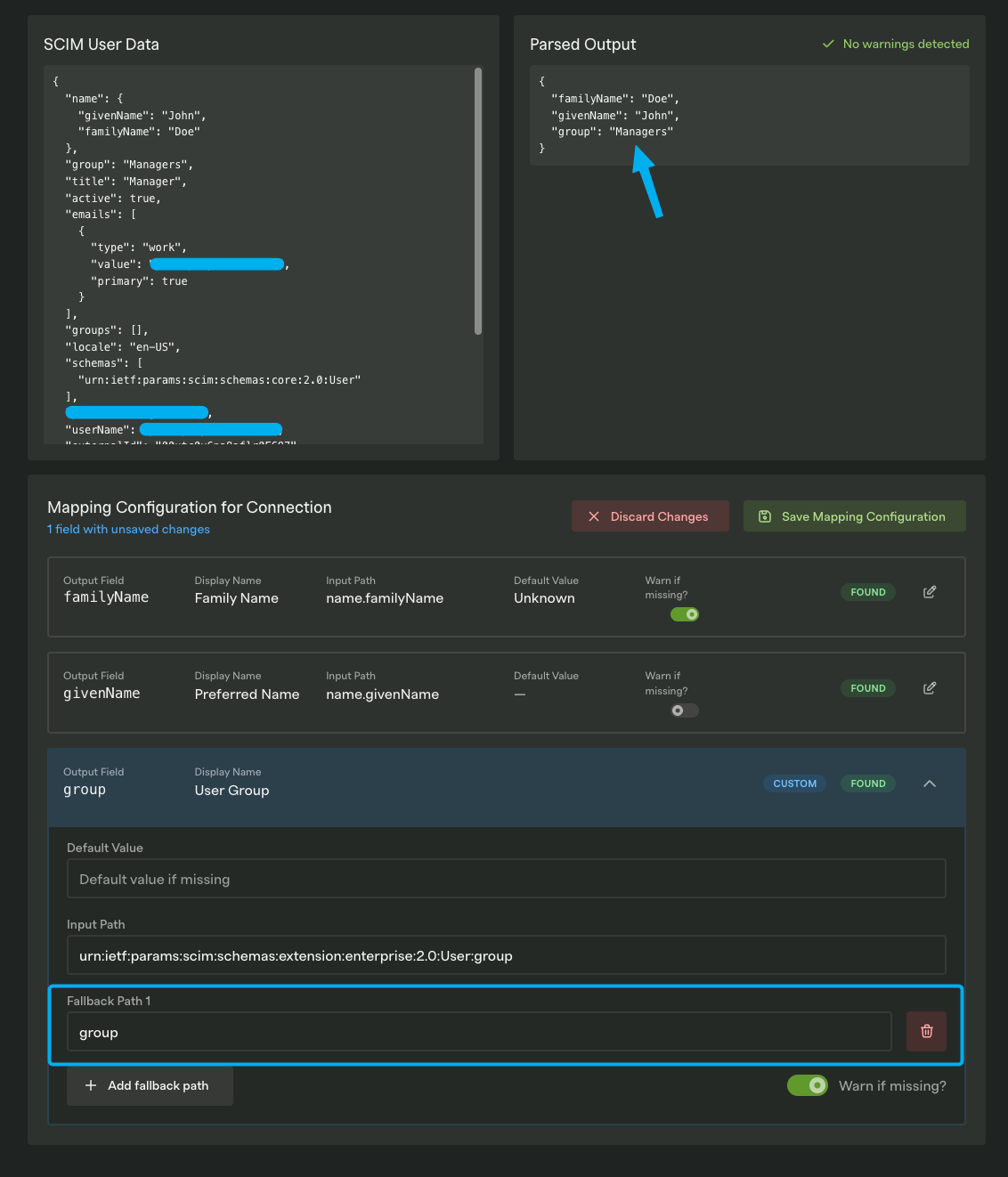
In the image above you can see that the group attribute could not be found but looking at the SCIM User Data we can see that the attribute has a value of Managers. So what’s wrong here? Let’s take a closer look at the group field lower down on that page.
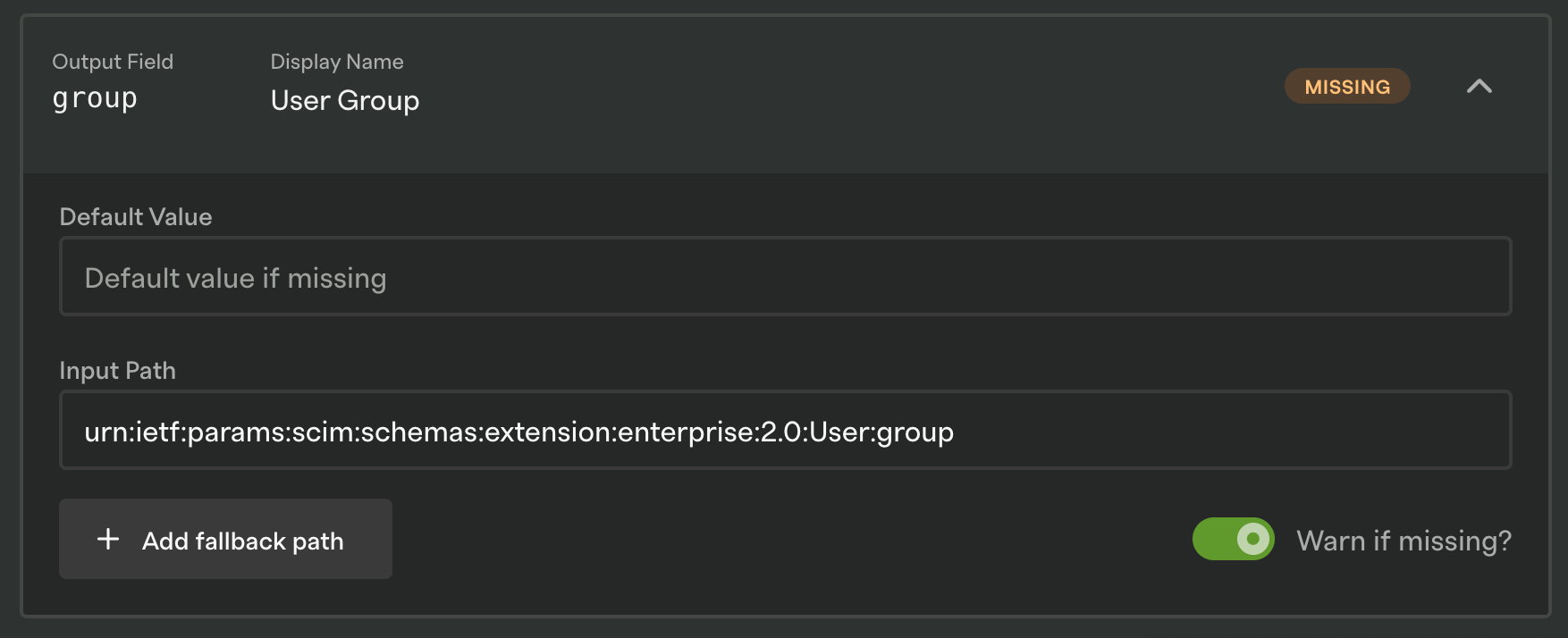
It looks like we’re searching the path urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:group for the property, which doesn’t seem to work for this user. Instead, let’s add a fallback path of group.
Using with SSO
Section titled “Using with SSO”Though SCIM and SSO can function separately, they work best when implemented together. SSO manages user authentication, while SCIM takes care of creating, updating, and managing user accounts and their attributes. Using SSO and SCIM together creates a comprehensive authentication and authorization solution that benefits both you and your users. See the Using SSO with SCIM docs for more information.